sercet management in k8s
how to use secret in k8s
- encryption method
| name | Description | Strength | Key Length |
|---|---|---|---|
| identity default | None | test | test |
| secretbox | XSalsa20 and Poly1305 | Strong | 32 byte |
| aesgcm | AES-GCM with random nonce | Must be rotated every 200k writes | 16, 24, 32-byte |
| aescbc | AES-CBC with PKCS#7 padding | Weak | 32-byte |
| kms | very complex | Strongest | 32 byte |
- define access resource
- PodSecurityPolicy
- RBAC
- Authentication
how to create secret resource
- create secret from kubectl command
- from file
- cmds
1
2
3kubectl create secret generic db-user-pass \
--from-file=./username.txt \
--from-file=./password.txt
- cmds
- from command line
-
1
2
3kubectl create secret generic db-user-pass \
--from-literal=username=devuser \
--from-literal=password='S!B\*d$zDsb='
-
- check secret
kubectl get secret db-user-pass -o jsonpath='{.data}'
- encode secretbox
kubectl delete secret <secret name>
- from file
- create secret from configurationgst
- create secret yaml file
- run
kubectl apply -f <your secert yaml>
how to use
- There are three main ways for a Pod to use a Secret:
- As files in a volume mounted on one or more of its containers.
- add a pod yaml to access to secret
- tips:
- add spec.volumeMount section to save the secrect
- add spec.volume to mount secret from pod and the should be same as the secretName
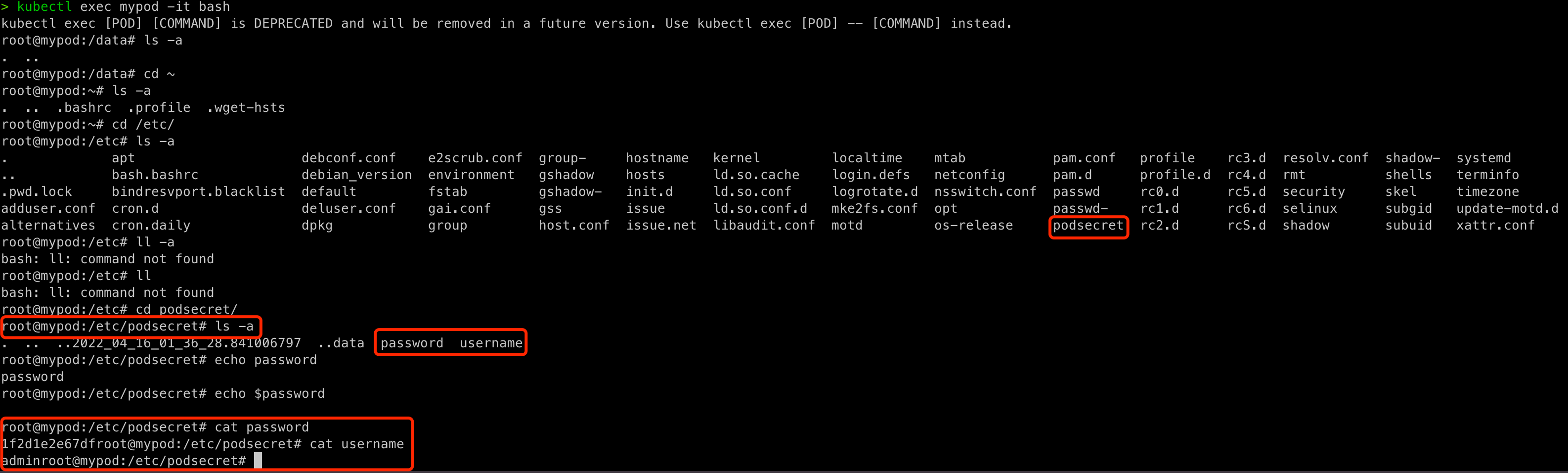
- use cmd
kubectl exec <pod name> -it bash, get into the pods and cd to /etc/podsecret
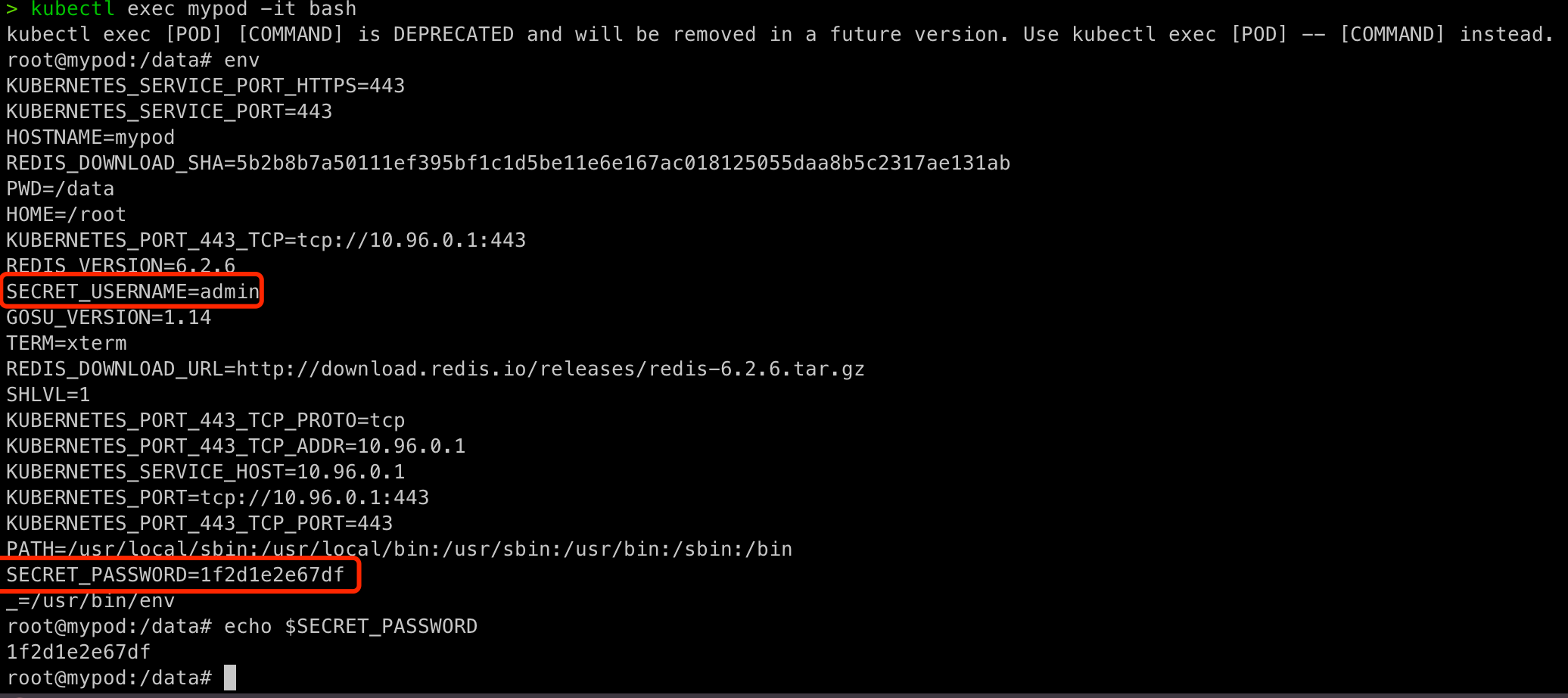
- As container environment variable.
- add env section

- add env section
- By the kubelet when pulling images for the Pod.
- As files in a volume mounted on one or more of its containers.
- Title: sercet management in k8s
- Author: Xiao Qiang
- Created at : 2023-03-05 15:03:29
- Updated at : 2025-08-06 15:16:17
- Link: http://fdslk.github.io/tech/ops/k8s/secret/2023/03/05/ops-k8s-secret/
- License: This work is licensed under CC BY-NC-SA 4.0.
Comments